Definitions Overview

IT Architecture
Before we head off into definitions and categorization, lets just ask the question of all questions..."Why does anyone need an IT Architecture?"

IT Risk
Rarely one can find a risk related discussion that is specific to IT risks and that reaches beyond IT Security. This is rather surprising given that most business processes today rely heavily on IT and that risk management is a hot topic in corporate governance as well as a major source of business for compliance consultants.

IT Security
Security provided by IT Systems can be defined as the IT system’s ability to being able to protect confidentiality and integrity of processed data. as well as to be able to provide availability of system (and subsequently the processed of data). Together they are referred to as the CIA characteristics (= qualities).

IT Security Architecture
This article derives a definition for IT Security Architecture by combining the suggestions from the previous articles.
Security Patterns
In this article we discuss how the evolution of design patterns has shaped the prevalent understanding of security patterns. We then analyse that particularly in the area of security the best practices are also manifested in other ways than only design patterns (e.g. Standard of Good Practice, Security Principles, and Control Catalogues). Finally we conclude that combining the idea of a structured controls catalogue and design patterns (as proposed by OSA) is particularly appealing and helps both the designer as well as the quality assuror and auditor.
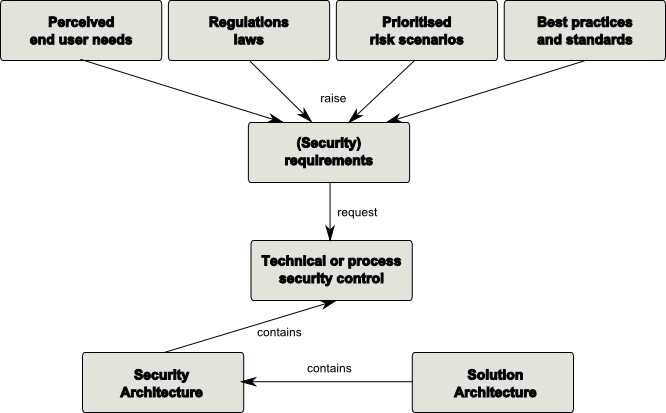
IT Security Requirements
IT Security Requirements describe functional and non-functional requirements that need to be satisfied in order to achieve the security attributes of an IT system.
